Which of the Following Are Real-life Examples of Cyber-attacks
15 Common Types of Cyber Attacks. Twitter users transferred the equivalent of at least 180000 in Bitcoin to scam accounts.

5 Real Life Data Breaches Caused By Insider Threats Ekran System
Your examples shall be from economyfinance sector.

. TCP SYN flood attack In this attack an attacker exploits the use of the buffer space during a Transmission Control Protocol TCP session initialization handshake. Man in the middle. While 83 percent of respondents say cyberattacks are among the top three threats facing organizations only 38 percent say they are prepared to experience one according to ISACAs 2015 Global.
WannaCry Ransomware Attack 2. The cyber attacks in December 2009 resulted in the companys re-evaluation of its business in the country. Curch of Scientology Attacked 7.
Which of the following are real-life examples of cyber-attacks select all that apply there are one to four correct answers. The man in the middle attack is where a cyber criminal is intercepting your data or information while it is being sent from one location to another ie. Malware is a type of application that can perform a variety of malicious tasks.
What were the consequences. Bangladesh Bank Cyber Heist 3. Hacking a pacemaker to deliver an 830 volt shock enough to kill a would-be victim.
That is for example if you are from say Department of Economics. Communications system to a server. The list of hacked accounts included those of Barack Obama Elon Musk Bill Gates Jeff Bezos Michael Bloomberg Apple Uber and other notable individuals and companies.
Phishing is an increasingly common cyberthreat. Types of CyberAttacks Top 10 Largest Cyber Attacks in the World 10. South Korea Credit Cards Data Compromise 9.
Malware Short for malicious software malware can refer to any kind of software no matter how its structured or operated. The ranking is presented in increasing order of impact based on number of victims. Adobe was going through hell.
There are different types of DoS and DDoS attacks. CovidLock ransomware 2020 Fear in relation to the Coronavirus COVID-19 has been widely exploited by cybercriminals. In 2012 researcher Barnarby Jack provided a real-life demonstration of what had been a theoretical risk for years.
MafiaBoy DDoS Attack on Amazon eBay CNN 8. While there are many different ways that an attacker can infiltrate an IT system most cyber-attacks rely on pretty similar techniques. Check out 11 real cases of malware attacks 1.
Depending on the type of malicious code malware could be used by hackers to steal or secretly copy sensitive data block access to files disrupt system operations or make systems inoperable. This type of ransomware infects victims via malicious files promising to offer more information about the disease. You are required to provide the following details.
----Chinese army officers suspected of being responsible for thousands of breaches of US. Ransomware spyware and Trojans are examples of malware. A denial of service DoS is a type of cyber attack that floods a computer or network so it cant respond to requests.
A distributed DoS DDoS does the same thing but the attack originates from a computer network. In 2015 in Ukraine a variant of the BlackEnergy malware made the first known successful cyberattack on a power grid disabling 30 substations and leaving hundreds of. German steel plant meltdown In 2015 using phishing emails to gain login credentials hackers wreaked havoc at a German steel mill by disrupting the control system and shutting down parts of the plant resulting in millions of dollars of damage.
Phishing in which hackers socially engineer email messages to entice recipients to open them. The main types of cyber threats are. The goal is to steal sensitive data like credit card and login information or to install malware on the victims machine.
In March 2010 Google relocated its servers for googlecn to Hong Kong in order to. The most common are TCP SYN flood attack teardrop attack smurf attack ping-of-death attack and botnets. CovidLock ransomware is an example.
Phishing is the practice of sending fraudulent communications that appear to come from a reputable source usually through email. Ashley Madison Data Breach 5. Below are some of the most common types of cyber-attacks.
There is strong evidence that the public transportation system needs dramatic investments in order to stay safe and sound from cyberattacks and the following three examples serve as real-life examples of what already exists and has occurred. Adobe announced in October 2013 the massive hacking of its IT infrastructure. Cyber attackers often use a flood attack to disrupt the handshake process and carry out a DoS.
Cyberattacks DDoS Threats to Air Transport Industry. Distributed denial of service DDoS Man in the Middle MitM Social engineering Malware and spyware Password attacks Advanced persistent threats APT We cover each of these threats in more. Below are a few examples of companies that have fallen victim and paid a high price for it.
This type of attack is very common with vulnerable Wi-Fi connections like at coffee shops hotels and restaurants. Sony PlayStation Network DDOS Attack 4. Here is our Top 10 of the worlds largest cyberattacks 10.
-Make some quality internet search and give two real life examples of cyber-attacksthat have taken place in the field of your major of study. Government and corporate websites.

5 Real Life Data Breaches Caused By Insider Threats Ekran System
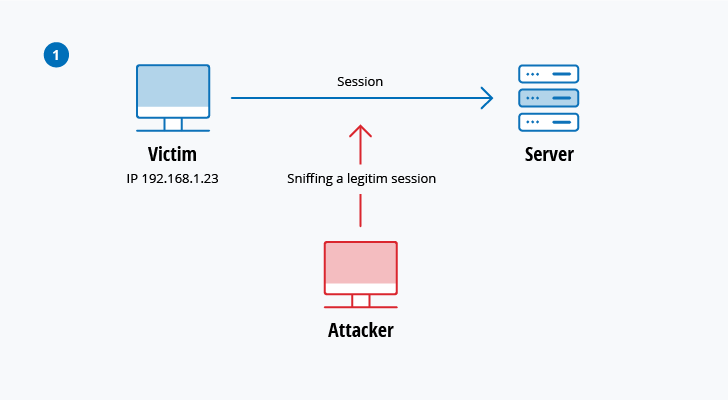
Top 10 Most Common Types Of Cyber Attacks
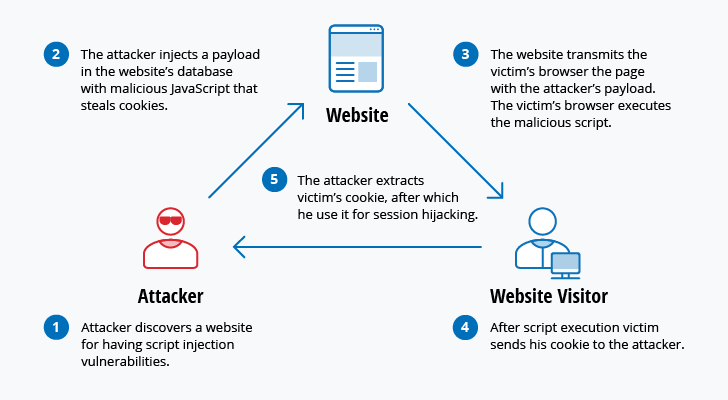
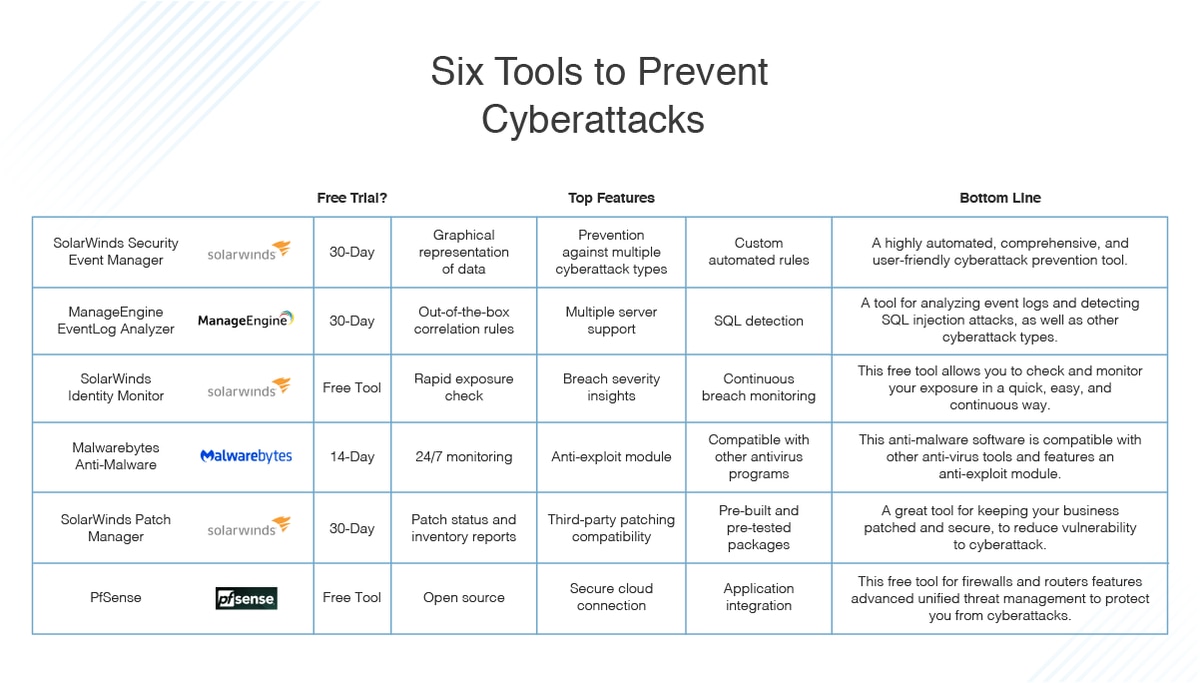
No comments for "Which of the Following Are Real-life Examples of Cyber-attacks"
Post a Comment